In many companies and organizations around the world, user’s identity data is stored and handled in centralized systems rather than decentralized ones. A centralized system comes with many risks, such as data leaks or users not being in control of their data. These problems can be fixed by using a decentralized system known as the Self-Sovereign Identity (SSI) system. SSI system is a user-centric system that lets users manage and control their ow
The Khmer script presents a unique challenge due to its distinct characters, which make recognizing handwriting especially challenging. This study tackles this challenge by creating a specialized computer program that recognizes handwritten Khmer text. Our goal is to enhance Khmer language education by offering a valuable tool that supports educators and students in improving their Khmer language proficiency. This user-friendly tool improves hand
This study investigates how machine learning (ML) and deep learning (DL) techniques can be used to predict student dropouts, which is a major issue for higher education institutions. Using a dataset from Kaggle titled “Predict students’ dropout and academic success,” we analyzed data from 4424 students across 17 undergraduate programs. We used 35 different attributes for each student’s profile, which gave us a strong basis for our predictive mode
5G mobile communication is based on three main pillars: enhanced mobile broadband, massive machine-type communication, and ultra-reliable low latency. For a mobile station (MS) to connect to a 5G network and access user data, it must first perform cell identification during the initial stage before establishing radio and network connections. This is done using the primary synchronization signal (PSS) and secondary synchronization signal (SSS) sen
Word spotting in Khmer printed documents presents a unique challenge due to the complexities of the Khmer script and the vast array of font styles employed. The scarcity of large, publicly available datasets further complicates this task. This work proposes a two-module approach for achieving accurate and efficient word spotting in Khmer documents. Separate datasets are utilized for text detection and recognition. The first module employs the sta
Abstract: In this paper, reinforcement learning, as a subfield of artificial intelligence and machine learning, is examined based on its capacity for interdependent statistics, optimization, and mathematical concepts and how agents can use trial-error learning to solve tasks. Furthermore, fine-tuning of parameters in machine learning is the ability of scientists to directly influence the architecture, usability, and effectiveness of models in fin
Identifying the writer of handwritten text poses a significant challenge due to the diversity and variability inherent in handwriting styles. This paper proposes a novel approach based on Siamese neural network (SNN) for the task of writer identification in Khmer handwriting. The SNN architecture was leveraged for training and testing on a dataset specifically collected for this purpose. The dataset comprised 1400 samples collected from students
As artificial intelligence has grown, a large language model is a model train with a vast quantity of textual data. This model can be tailored to a particular task, such as chatbots, text production, and question-answering. However, most of the existing pre-trained models nowadays were trained with English datasets, leading to limited support and low performance in other languages, especially low-resource languages like Khmer. To address the imba
Artificial intelligence, fueled by machine learning and deep learning techniques, is revolutionizing various domains. Reinforcement learning (RL) stands out as a potent method for training agents to navigate complex environments and make informed decisions. Our focus is on applying RL techniques, specifically Convolutional Neural Networks (CNNs) combined with policy gradient methods, to enhance the gameplay experience of Khmer chess. Our goal is
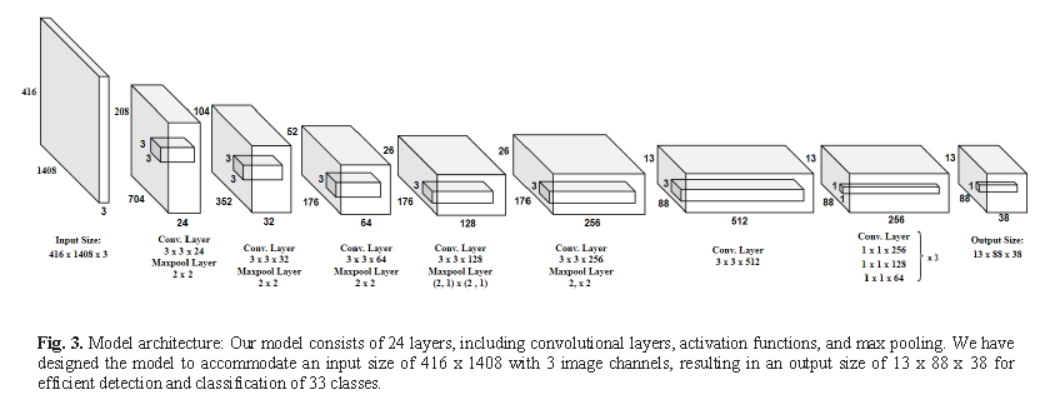
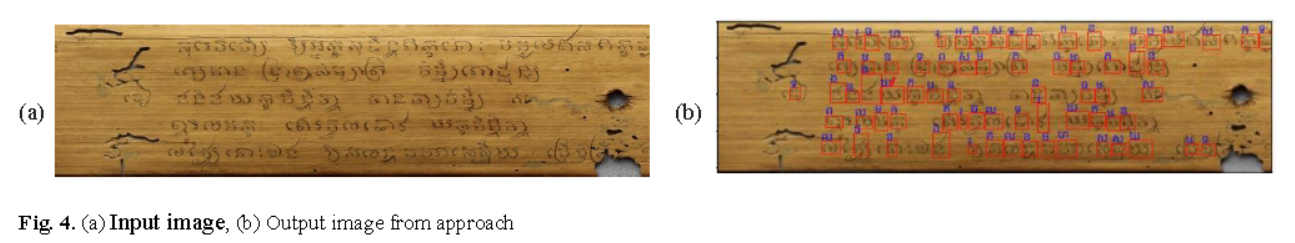
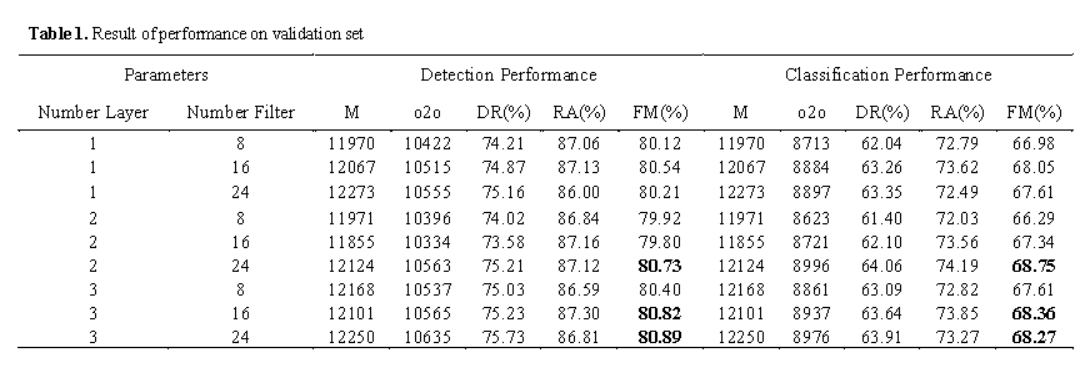
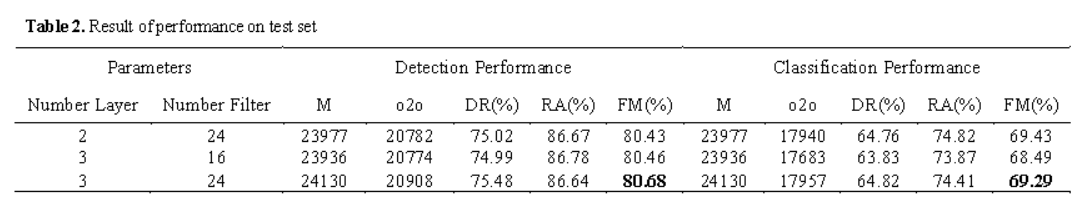
Word spotting plays a crucial role in document analysis, particularly for ancient palm leaf manuscripts. Khmer palm leaf manuscripts, which are written on rectangularly cut and dried palm leaf sheets, hold significant cultural value in Cambodia. These manuscripts contain valuable historical, religious, and linguistic information, making their preservation essential. However, extracting information from them is challenging due to their fragility,